The earliest antivirus utilities recognized malware by consulting a database of signatures. These signatures were elements of malware files that remained invariant, and hence could be used for identification. Malware writers quickly learned to write polymorphic programs that mutate slightly with each new copy, foiling simple signature-based detection. In any case, the never-ending proliferation of malware would have required an always-growing database. Webroot SecureAnywhere AntiVirus avoids the whole problem by using a completely different technique. When it encounters an unknown app, it runs it in a bubble, preventing the app from making any permanent system changes until its cloud-based intelligence reaches a conclusion about the program. If it’s malicious, the tiny local Webroot program wipes out the attacker and reverses its actions. It’s a different approach from most competitors, but our tests show that it works well.
How Much Does Webroot SecureAnywhere AntiVirus Cost?
Price-wise, Webroot runs with the pack. Like Bitdefender, Kaspersky, and several others, it costs just under $40 for a one-year subscription. Where a three-license Webroot subscription cost $10 more, the other two ask another $20 for a three-pack. Norton’s standalone antivirus doesn’t have a multi-license plan, and one license will run you $59.99. As for McAfee AntiVirus Plus, it also costs $59.99 per year, but that subscription gets you unlimited protection for your Windows, macOS, Android, and iOS devices. As always, you may find any of these prices discounted for the first year, sometimes quite deeply.
You can use your Webroot licenses to install antivirus on both PCs and Macs. Some components of Webroot SecureAnywhere Antivirus (for Mac), in particular the web-based protection system, are identical on both platforms. Overall, the two products offer similar security features, though Webroot doesn’t go quite as overboard with expert features on the Mac.
Webroot’s installer is tiny, less than 6MB, and it installs in a flash. Immediately on installation, it busies itself with a collection of startup tasks, checking off each one as it finishes. Among the listed tasks are: scanning for active malware; analyzing installed applications to reduce warnings and prompts; establishing a system baseline; and optimizing performance for your unique system configuration. Even with these added tasks, the process goes quickly.
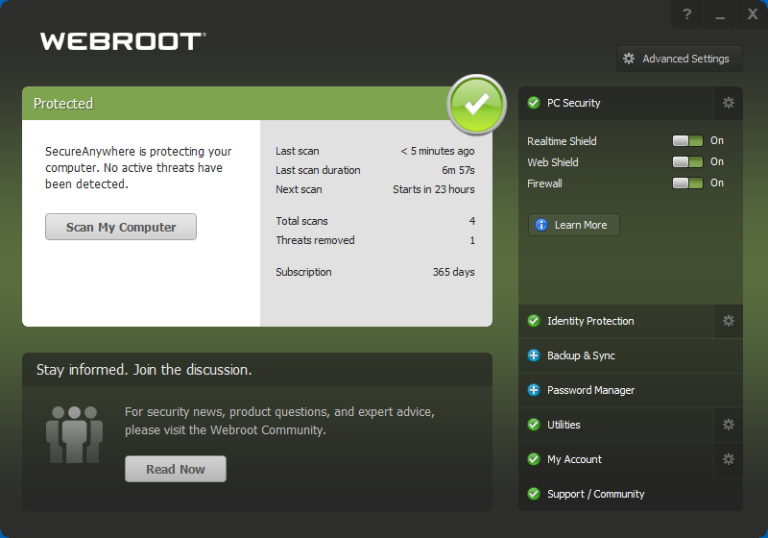
The product’s appearance hasn’t changed appreciably in quite a while. Its green-toned main window features a lighter panel that includes statistics about recent scans and a button to launch an on-demand scan. Even if you never click that button, Webroot makes a full scan during installation and runs a scheduled scan every day. A panel at the right manages access to the rest of this product’s significant collection of security features.
Online Console
As part of getting started with Webroot, you’ll set up a profile online. The process has a strong emphasis on security. I don’t always use the strongest passwords for profiles used in testing, since they’re only needed for the duration of the test. But Webroot required a truly strong password and wouldn’t accept anything less. In addition, it requires a secondary security code that you enter in an unusual fashion. Each time you log in to the online profile, it demands two specific characters from that security code, different each time. It might ask for the 2nd and 4th characters on one visit, the 6th and 7th on another.
As if that weren’t enough security, Webroot strongly encourages you to set up two-factor authentication. You set up 2FA in the usual fashion, scanning a QR code with Google Authenticator or a workalike. If you do choose to establish 2FA, it replaces the security code requirement. No more counting on your fingers to come up with the right characters!
There’s a lot you can do in the online console. If you haven’t used all your licenses, you can log in and click a button to add protection to another device. You can select any device and view scan results, including the filename and malware class of removed threats. And you can send remote control commands to the device.
There’s a lot you can do in the online console. If you haven’t used all your licenses, you can log in and click a button to add protection to another device. You can select any device and view scan results, including the filename and malware class of removed threats. And you can send remote control commands to the device.
The ability to launch a scan remotely is clearly a big plus. You can also lock, shut down, or restarts the computer. And if you’ve removed Webroot from an old computer, you can use the command system to deactivate it, freeing up that license for use on another PC or Mac.
Lab Test Difficulties
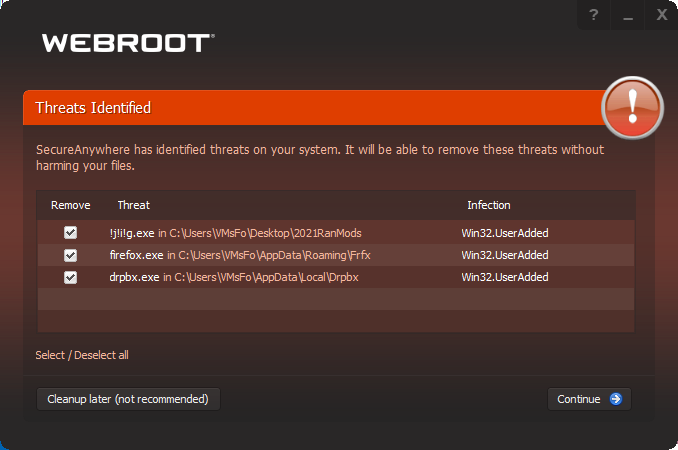
As noted, Webroot handles new, unknown programs by letting them run under strict monitoring. It prohibits irreversible actions like sending personal data to the internet, and keeps a journal of reversible actions, all while awaiting a verdict from Webroot’s cloud analysis system. If the program under judgment proves to be nasty, Webroot wipes it out and reverses all its journaled changes.
This system just isn’t compatible with many independent lab tests. Labs like AV-Test Institute(Opens in a new window) and AV-Comparatives expect antivirus programs to act right away on malware they recognize, whether detection occurs using signatures, heuristics, or behavioral analysis. Webroot’s relationship with the labs has been rocky. Just one of the four that I follow has recently included Webroot in testing.
Aggregate Lab Results
Researchers at MRG-Effitas report on two main tests, one specific to banking Trojans and one aiming to cover the full range of malware types. Security programs that don’t earn near-perfect scores simply fail; these are tough tests. Webroot used to do particularly well in the all-types test, which offers certification to products that remediate all malware attacks within 24 hours. That sort of test aligns well with Webroot’s journal-and-rollback system. Alas, it’s been some years since Webroot participated in this test.
Researchers at SE Labs(Opens in a new window) use a capture and replay system to package up real-world malware attacks and unleash them on multiple antivirus products simultaneously. This lab certifies antivirus products at five levels, AAA, AA, A, B, and C; Webroot earned a respectable AA certification. To be fair, all but one of the tested products came in at either the AAA or AA level. The odd man out was Malwarebytes Premium, which earned a B. Like Webroot, Malwarebytes doesn’t always align well with standard testing methods.
I use an algorithm to derive an aggregate lab score for products tested by at least two labs. With just one result, Webroot doesn’t have an aggregate score.
As ever, Bitdefender Antivirus Plus and Kaspersky take perfect or near-perfect scores from the labs. With perfect scores from all four labs, Kaspersky boasts a perfect 10 points. Tested by three labs, AVG holds an impressive 9.9 points, with Bitdefender and ESET NOD32 Antivirus close behind at 9.8 points.
Excellent Malware Protection
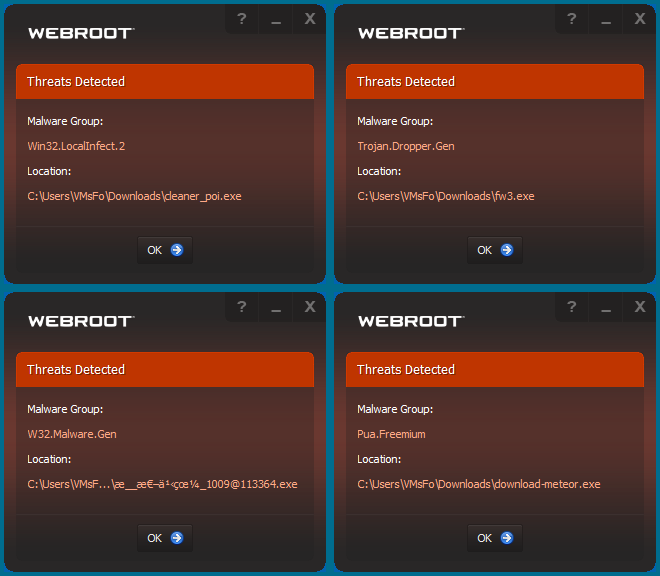
For some years now, Webroot has done very well in my own hands-on malware protection tests, though it handles them differently from most other products. It doesn’t react when I simply open a folder full of samples, or copy them to a new location. Rather, it checks each process as it launches.
In many cases, Webroot recognized and quarantined the sample almost immediately. Other samples ran for a while under Webroot’s restrictions, only to be wiped out a little later. After each malware removal event, Webroot asked to scan the system again to make sure it left no traces behind.
Frequently this secondary scan turned up another sample or two, in a kind of chain reaction. On removing the new-found threats, it wanted to scan yet again. The thought of enduring scan after scan might sound tedious, but each scan just took five to 10 minutes. That’s no big deal for the average user. On the other hand, at just five minutes apiece my collection of almost six dozen samples would have taken six hours. To keep the time reasonable, I settled on running the samples in groups of five, postponing cleanup for the first four of each group.
Whether by detection on launch or through a chain reaction capture, Webroot detected 99% of my samples and scored 9.8 of 10 possible points. PC Matic Home nominally scored the same, but its default-deny system doesn’t actively detect most malware. Rather, it simply detects that the program isn’t on its whitelist. That’s why PC Matic’s scores have an asterisk in the chart below.
McAfee and Malwarebytes did beat Webroot’s scores, by a hair. Tested with this same sample set, they both detected every single sample. Malwarebytes scored a perfect 10, and McAfee came close with 9.9 points.
Webroot’s scan also put a couple of my hand-coded testing tools in the cooler, but I can’t really blame it. Here you have a program that’s never been seen before by the cloud analysis system, and its purpose is to launch fraudulent URLs. Suspicious much? I restored my tools from quarantine and proceeded with testing.
Malware Protection Tests
I use the same set of curated samples for months, because the collection process itself takes weeks. To get a look at protection against the latest threats, I start with a feed of URLs that researchers at MRG-Effitas(Opens in a new window) recently found to be hosting malware. Typically, these are no more than a couple days old. I launch each and note whether the antivirus prevents browser access to the dangerous URL, eliminates the file upon download, or completely fails to notice the malware download.
Of more than 100 validated dangerous URLs, Webroot blocked 85% in the browser and wiped out the malware payload of another 11%, for a total of 96% protection.
That’s quite a good score, though eight recent products have done even better. Yes, each product gets hit with a different selection of malware-hosting URLs, but they’re always the most recent ones. McAfee leads the pack, with 100% protection. Bitdefender, G Data, and Sophos all came close with 99%. I’m pleased the success stories from Webroot and the rest. What better time to quash malware than before it even lands on your PC?
Phishing Protection Triumph
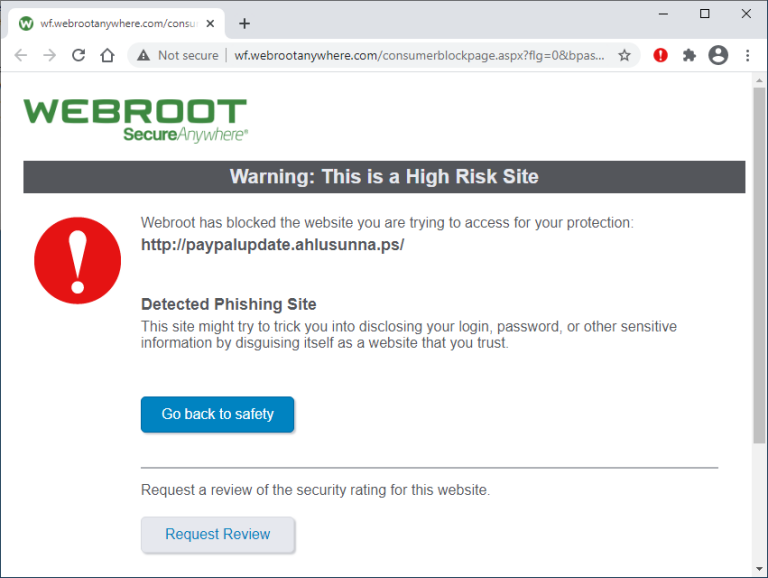
There’s nothing innately dangerous about a phishing website—no drive-by downloads, malicious scripts, or other active threats, just an inviting imitation of a secure website. You’re perfectly safe if you’re astute enough to recognize and avoid the fraudulent page. But woe betide the careless web surfer who enters login credentials on one of these fraudulent sites. If you fall for the fraud, you’ve just given away full access to your bank site, shopping site, even dating site. It’s not good.
These fraudulent sites get shut down and blacklisted quickly, but the perpetrators simply pop up another fake and start trolling for new victims. To test an antivirus product’s phishing protection, I try for an even split between verified phishing URLs and reported frauds that are so new there’s been no time to analyze and blacklist them. I launch each URL in a browser protected by the product in question, and simultaneously in browsers relying on the phishing protection built into Chrome, Edge, and Firefox. I discard any that fail to load in one or more of the browsers, and any that don’t precisely fit the definition of phishing. Once I have enough data points, I run the numbers.
Phishing Protection Tests
Webroot blocked 99% of the verified frauds and outperformed all three of the browsers—an impressive showing. Bitdefender and Norton also scored 99% in their own tests, while F-Secure Anti-Virus and McAfee managed 100%.
Phishing is totally platform independent. If your smart fridge includes a full-scale browser, you can get scammed while making a shopping list. Phishing protection, though, can vary by platform. In the past I’ve frequently seen situations where a company’s Windows product outperformed its macOS product in exactly the same test. With Webroot, the Windows and Mac products scored almost in lockstep, but the Mac edition did just a fraction better, scoring 100%.
See How We Test Security Software
Mixed Results in Ransomware Experiments
The journal and rollback system that Webroot uses can even roll back the effects of encrypting ransomware, though the company warns that limitations, such as available drive space, can impact this ability. In truth, it would be very unusual for a ransomware attack to get past all the other layers of protection. Webroot wiped out all my ransomware samples, most by recognizing them as known bad programs, a few by noticing bad behavior after launch. I had to scramble to figure out how to test its ransomware protection.
My coding skills are rusty; there’s no way I could write a never-before-seen encrypting ransomware specimen, even if I wanted to. For testing, I wrote a simple-minded ransomware simulator that encrypts all text files in the document folder using reversible XOR encryption. Webroot had already encountered this simulator in previous reviews, so it wiped out the app on launch. To avert that effect, I modified the program, changing its name, length, and a few non-executable bytes.
The newly disguised program ran unhindered, and I verified that it did encrypt the target files. In Webroot’s Active Processes list, I found the program running in Monitored mode, meaning Webroot was keeping detailed track of its activity. Rather than waiting for a decision from Webroot’s cloud-based brain, I cut to the chase. In the processes list I blocked the program, confirmed immediate termination, and launched a scan. The scan removed the file and reversed its actions, restoring the encrypted files, just as I had hoped.
Webroot’s monitoring system works with all malware types. A similar feature in Trend Micro Antivirus+ Security focuses just on ransomware. At the first sign of ransomware behavior, it backs up important files. If its behavioral detection verifies a ransomware attack, it terminates the malware and restores the backed-up files.
That little experiment with a hand-modified version of my ransomware simulator inspired me to try testing with hand-modified versions of actual file-encrypting malware samples. Results were mixed. Out of 10 file encrypting ransomware samples, Webroot detected that two were trying to modify the Registry to launch at boot. When I blocked those actions, the samples did not go on to encrypt files. Three others launched but did nothing. That could be due to the program detecting Webroot’s presence. It’s also possible that by modifying the files I triggered some internal integrity check.
Webroot didn’t stop any of the other five from encrypting files or posting ransom notes. I treated each of these the way I did my own simulator. Looking at the Active Processes list, I saw just one process in the Monitor state, so I blocked that one and then ran a scan to undo its activity. As far as I could tell, it completely restored the files encrypted by three of the samples. It didn’t remove any ransom notes, though, and it left the encrypted version of the files in place. In addition, all the recovered files got their date/time stamp reset to the moment of recovery.
As for the other two, Webroot apparently failed to journal their dirty deeds. After a full scan, the encrypted files remained encrypted, with no recovery of their original versions.
You’re almost certainly not going to be hit by a ransomware attack that some rando modified by hand. However, this test does emulate what would happen if you encountered a ransomware sample that Webroot’s analysis system had never seen before. And what would happen isn’t great. Do keep in mind, though, that unknowns quickly become known. Whey I tried to launch the same hand-modified samples a day later, Webroot eliminated them all immediately on launch.
Helpful Firewall
For many security companies, the addition of a personal firewall is one of the features that distinguishes the security suite from the standalone antivirus. Webroot’s antivirus includes a firewall, but it doesn’t work quite the same as most. It makes no attempt to put your system’s ports in stealth mode, leaving that task to the built-in Windows Firewall. That’s fine; the built-in does a good job. The only time a firewall’s stealth abilities matter is if they take over from Windows Firewall and don’t do a proper job.
Webroot classifies programs as good, bad, or unknown. Like Norton AntiVirus Plus, it leaves the good ones alone, eliminates the bad ones, and monitors the unknowns. As mentioned earlier, if a monitored unknown program tries a non-reversible action like sending your credit card details overseas, Webroot prevents it.
By default, the firewall ups its game when Webroot detects an active infection, which causes the main window to turn from green to dramatic red. In this mode, any network traffic by unknown programs requires your permission, but normal activities like Web browsing proceed uninterrupted.
In past evaluations I’ve been able to see the firewall in action by tweaking its settings to warn every time an unknown program attempts internet access, not just when an infection is present, or by setting it to warn for every process that isn’t already trusted. This time around, I found that those changes had no effect. Checking with my contact at Webroot, I learned that a recent update introduced a bug such that the firewall is disabled. A fix is expected in two to three weeks. I’m surprised that a problem of this magnitude got past the quality assurance process.
Of course, firewall protection means bubkes if a malware coder can reach in and turn it off. The more processes and services a security tool contains, the more opportunities for such chicanery. With one service, two processes, and no settings exposed in the Registry, Webroot is buttoned up tight. My every attempt to halt its protection resulted in an ignominious “Access Denied” message.
For Experts Only
Like most modern antivirus utilities, Webroot works fine even if you totally ignore it. It comes configured for maximum protection, and if you don’t make any changes, it runs a scan every day. What more could you want? It turns out that there’s a ton more to discover under the surface, but only if you want to.
Clicking the settings gear next to Identity Protection on the main window brings up a page with controls that toggle what it calls Phishing Shield and Identity Shield. The rest of the page displays a laundry list of just what these shields involve. They aim to fend off a wide variety of typical malware attacks including man-in-the-middle, browser process modification, and keylogging.
Identity Shield and Phishing Shield appear on the Online Protection page under Identity Protection. The adjacent Application Protection page lists apps that get special attention from Webroot. Specifically, it aims to ensure that your personal information can’t be extracted from these programs. On my test system, Webroot populated the list with Internet Explorer, Firefox, and two versions of Chrome. Oddly, one of the Chrome entries referred to a non-existent folder.
You can also add programs to the list for protection. Edge seemed like an obvious choice, so I added it. Its entry in the list of protected applications also referenced a non-existent folder, not the folder from which I selected it. My Webroot contact explained that while this does look odd, it doesn’t mean that the apps in question aren’t protected. Webroot’s cloud-based master file system renders those randomized temporary paths into the correct path.
Clicking the gear icon next to Utilities reveals a set of antimalware tools that let you repair damage left behind after malware remediation, things like malware-modified desktop background, screensaver, or system policies. You can also use it to quickly reboot into Safe Mode, or to perform an instant reboot. Those with the necessary skills can use another tool to manually remove any program, along with its associated Registry data. Even if you claim no tech skills yourself, you can run a removal script created by Webroot tech support.
If you really want to see what Webroot has been doing, open the Reports page and check its current or historical activity. You probably won’t want to read the available scan log or threat log, but tech support might well ask for them.
The System Control page is where you find the Active Processes list, which shows all running processes and flags those that are under monitoring by Webroot. Also on this page is the SafeStart Sandbox. There are features for experts, and features for professionals. SafeStart Sandbox is among the latter. If you’re a trained antivirus researcher, you can use it to launch a suspect program under detailed limitations that you specify. If you’re not, just leave it alone. I don’t even use that one myself.
Small Is Beautiful
Opening the folder containing a typical antivirus or security suite reveals amazing number of files and folders. When I check system free space before and after installing security suites, I find that most occupy a gigabyte or two of disk space, or even more.
As for Webroot, it’s ridiculously small. Open its folder and you find just one significant file, WRSA.exe, with a size less than 6MB. That’s tiny! As noted, Task Manager reveals just two Webroot processes. Norton also packs its protection into two processes, while others require more. During one test, I found 17 active processes for McAfee, for example. Webroot relies on just one Windows service, but some others run to 10 or more.
Just because a product uses more of processes or services doesn’t necessarily mean it’s eating up more of your system resources. It’s conceivable that a program with just one resource-hungry process could overload your system. Conceivable, but unlikely. By every measure I’ve found, Webroot remains the smallest antivirus around.
Still a Winner
Webroot SecureAnywhere AntiVirus doesn’t jibe with the testing methods used by many of the independent testing labs, though it earned a high score in one recent test. In our hands-on testing, it earned near-perfect scores both for malware protection and phishing detection. Its score against malware-hosting URLs was also quite good.
On the negative side, its ability to protect against never-before-seen ransomware proved uneven in testing, and as of this writing, its firewall component isn’t working. We also encountered a few glitches when testing the macOS version of this program. For now, we’re assuming these bumps will be ironed out. Webroot remains an antivirus Editors’ Choice winner, sure to please those who want good things in a small package.
Kaspersky Anti-Virus and Bitdefender Antivirus Plus routinely earn perfect or near-perfect scores from the antivirus testing labs, and both come with a panoply of useful bonus features. McAfee AntiVirus Plus doesn’t always score as high in lab tests or our own tests, but it’s a bargain, offering protection for every Windows, macOS, Android, and iOS device in your household. These three tools round out our collection of Editors’ Choice antivirus products, each with its own special merits.